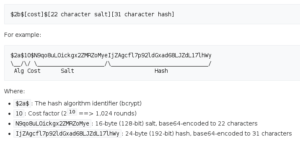
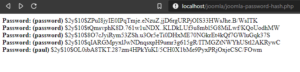
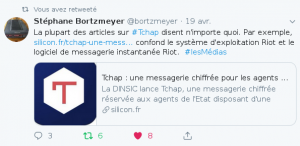
Posted on 28 octobre 2021.
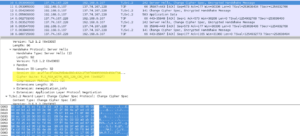
1- Etape 1 avec un certificat autosigné :
root@debian:/home/ensibs# apt-get install apache2
Reading package lists… Done
Building dependency tree… Done
Reading state information… Done
The following additional packages will be installed:
apache2-data apache2-utils ssl-cert
Suggested packages:
apache2-doc apache2-suexec-pristine | apache2-suexec-custom
The following NEW packages will be installed:
apache2 apache2-data apache2-utils ssl-cert
0 upgraded, 4 newly installed, 0 to remove and 1 not upgraded.
Need to get 706 kB of archives.
After this operation, 2,057 kB of additional disk space will be used.
Do you want to continue? [Y/n] Y
Get:1 http://deb.debian.org/debian bullseye/main amd64 ssl-cert all 1.1.0+nmu1 [21.0 kB]
Get:2 http://security.debian.org/debian-security bullseye-security/main amd64 apache2-data all 2.4.51-1~deb11u1 [160 kB]
Get:3 http://security.debian.org/debian-security bullseye-security/main amd64 apache2-utils amd64 2.4.51-1~deb11u1 [255 kB]
Get:4 http://security.debian.org/debian-security bullseye-security/main amd64 apache2 amd64 2.4.51-1~deb11u1 [270 kB]
Fetched 706 kB in 1s (1,332 kB/s)
Preconfiguring packages …
Selecting previously unselected package apache2-data.
(Reading database … 162254 files and directories currently installed.)
Preparing to unpack …/apache2-data_2.4.51-1~deb11u1_all.deb …
Unpacking apache2-data (2.4.51-1~deb11u1) …
Selecting previously unselected package apache2-utils.
Preparing to unpack …/apache2-utils_2.4.51-1~deb11u1_amd64.deb …
Unpacking apache2-utils (2.4.51-1~deb11u1) …
Selecting previously unselected package apache2.
Preparing to unpack …/apache2_2.4.51-1~deb11u1_amd64.deb …
Unpacking apache2 (2.4.51-1~deb11u1) …
Selecting previously unselected package ssl-cert.
Preparing to unpack …/ssl-cert_1.1.0+nmu1_all.deb …
Unpacking ssl-cert (1.1.0+nmu1) …
Setting up ssl-cert (1.1.0+nmu1) …
Setting up apache2-data (2.4.51-1~deb11u1) …
Setting up apache2-utils (2.4.51-1~deb11u1) …
Setting up apache2 (2.4.51-1~deb11u1) …
Enabling module mpm_event.
Enabling module authz_core.
Enabling module authz_host.
Enabling module authn_core.
Enabling module auth_basic.
Enabling module access_compat.
Enabling module authn_file.
Enabling module authz_user.
Enabling module alias.
Enabling module dir.
Enabling module autoindex.
Enabling module env.
Enabling module mime.
Enabling module negotiation.
Enabling module setenvif.
Enabling module filter.
Enabling module deflate.
Enabling module status.
Enabling module reqtimeout.
Enabling conf charset.
Enabling conf localized-error-pages.
Enabling conf other-vhosts-access-log.
Enabling conf security.
Enabling conf serve-cgi-bin.
Enabling site 000-default.
Created symlink /etc/systemd/system/multi-user.target.wants/apache2.service → /lib/systemd/system/apache2.service.
Created symlink /etc/systemd/system/multi-user.target.wants/apache-htcacheclean.service → /lib/systemd/system/apache-htcacheclean.service.
Processing triggers for man-db (2.9.4-2) …
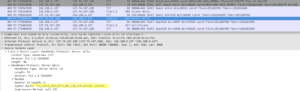
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:0c:52:89 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.101/24 brd 192.168.56.255 scope global dynamic noprefixroute enp0s3
valid_lft 589sec preferred_lft 589sec
inet6 fe80::a00:27ff:fe0c:5289/64 scope link noprefixroute
valid_lft forever preferred_lft forever
root@debian:/home/ensibs# cd /var/lib/apache2/
root@debian:/var/lib/apache2# ls
conf module site
root@debian:/var/lib/apache2# cd conf
root@debian:/etc/apache2# ls
apache2.conf conf-available conf-enabled envvars magic mods-available mods-enabled ports.conf sites-available sites-enabled
root@debian:/etc/apache2# vi apache2.conf
root@debian:/etc/apache2# cd mods-enabled/
root@debian:/etc/apache2/mods-enabled# ls
access_compat.load auth_basic.load authz_core.load autoindex.conf deflate.load env.load mime.load negotiation.conf reqtimeout.load status.conf
alias.conf authn_core.load authz_host.load autoindex.load dir.conf filter.load mpm_event.conf negotiation.load setenvif.conf status.load
alias.load authn_file.load authz_user.load deflate.conf dir.load mime.conf mpm_event.load reqtimeout.conf setenvif.load
root@debian:/etc/apache2/mods-enabled# cd ..
root@debian:/etc/apache2# cd mods-available/
root@debian:/etc/apache2/mods-available# ls
access_compat.load authz_core.load cgi.load expires.load ldap.conf negotiation.load proxy_uwsgi.load socache_dbm.load
actions.conf authz_dbd.load charset_lite.load ext_filter.load ldap.load proxy_ajp.load proxy_wstunnel.load socache_memcache.load
actions.load authz_dbm.load data.load file_cache.load log_debug.load proxy_balancer.conf ratelimit.load socache_redis.load
alias.conf authz_groupfile.load dav_fs.conf filter.load log_forensic.load proxy_balancer.load reflector.load socache_shmcb.load
alias.load authz_host.load dav_fs.load headers.load lua.load proxy.conf remoteip.load speling.load
allowmethods.load authz_owner.load dav.load heartbeat.load macro.load proxy_connect.load reqtimeout.conf ssl.conf
asis.load authz_user.load dav_lock.load heartmonitor.load md.load proxy_express.load reqtimeout.load ssl.load
auth_basic.load autoindex.conf dbd.load http2.conf mime.conf proxy_fcgi.load request.load status.conf
auth_digest.load autoindex.load deflate.conf http2.load mime.load proxy_fdpass.load rewrite.load status.load
auth_form.load brotli.load deflate.load ident.load mime_magic.conf proxy_ftp.conf sed.load substitute.load
authn_anon.load buffer.load dialup.load imagemap.load mime_magic.load proxy_ftp.load session_cookie.load suexec.load
authn_core.load cache_disk.conf dir.conf include.load mpm_event.conf proxy_hcheck.load session_crypto.load unique_id.load
authn_dbd.load cache_disk.load dir.load info.conf mpm_event.load proxy_html.conf session_dbd.load userdir.conf
authn_dbm.load cache.load dnssd.conf info.load mpm_prefork.conf proxy_html.load session.load userdir.load
authn_file.load cache_socache.load dnssd.load lbmethod_bybusyness.load mpm_prefork.load proxy_http2.load setenvif.conf usertrack.load
authn_socache.load cern_meta.load dump_io.load lbmethod_byrequests.load mpm_worker.conf proxy_http.load setenvif.load vhost_alias.load
authnz_fcgi.load cgid.conf echo.load lbmethod_bytraffic.load mpm_worker.load proxy.load slotmem_plain.load xml2enc.load
authnz_ldap.load cgid.load env.load lbmethod_heartbeat.load negotiation.conf proxy_scgi.load slotmem_shm.load
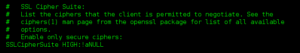
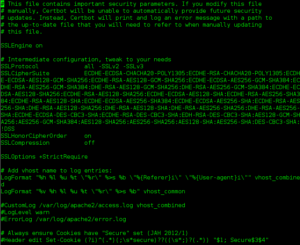
root@debian:/etc/apache2/mods-available# vi ssl.conf
root@debian:/etc/apache2/mods-available# cd ..
root@debian:/etc/apache2# vi apache2.conf
root@debian:/etc/apache2# a2enmod ssl
Considering dependency setenvif for ssl:
Module setenvif already enabled
Considering dependency mime for ssl:
Module mime already enabled
Considering dependency socache_shmcb for ssl:
Enabling module socache_shmcb.
Enabling module ssl.
See /usr/share/doc/apache2/README.Debian.gz on how to configure SSL and create self-signed certificates.
To activate the new configuration, you need to run:
systemctl restart apache2
root@debian:/etc/apache2# a2ensite default-ssl
Enabling site default-ssl.
To activate the new configuration, you need to run:
systemctl reload apache2
root@debian:/etc/apache2# service apache2 reload
root@debian:/etc/apache2# mkdir tls
root@debian:/etc/apache2# cd tls
root@debian:/etc/apache2# ls
apache2.conf conf-available conf-enabled envvars magic mods-available mods-enabled ports.conf sites-available sites-enabled tls
root@debian:/etc/apache2# chmod 600 tls/*.*
root@debian:/etc/apache2# ls
apache2.conf conf-available conf-enabled envvars magic mods-available mods-enabled ports.conf sites-available sites-enabled tls
root@debian:/etc/apache2# cd sites-enabled/
root@debian:/etc/apache2/sites-enabled# ls
000-default.conf default-ssl.conf
root@debian:/etc/apache2/sites-enabled# vi default-ssl.conf
root@debian:/etc/apache2/sites-enabled# cd /etc/ssl
root@debian:/etc/ssl# ls
certs openssl.cnf private
root@debian:/etc/ssl# ls -lart
total 44
-rw-r–r– 1 root root 11118 Aug 24 10:28 openssl.cnf
drwxr-xr-x 4 root root 4096 Oct 19 14:52 .
drwx–x— 2 root ssl-cert 4096 Oct 27 18:04 private
drwxr-xr-x 2 root root 12288 Oct 27 18:04 certs
drwxr-xr-x 119 root root 12288 Oct 27 18:21 ..
root@debian:/etc/ssl# vi openssl.cnf
root@debian:/etc/ssl# cd /etc/apache2/tls/
root@debian:/etc/apache2/tls# cd /etc/ssl
root@debian:/etc/ssl# ls
certs openssl.cnf private
root@debian:/etc/ssl# less openssl.cnf
root@debian:/etc/ssl#
root@debian:/etc/ssl# vi openssl.cnf
root@debian:/etc/ssl# cd /etc/apache2/sites-enabled/
root@debian:/etc/apache2/sites-enabled# ls
000-default.conf default-ssl.conf
root@debian:/etc/apache2/sites-enabled# vi default-ssl.conf
root@debian:/etc/apache2/sites-enabled# service apache2 restart
root@debian:/etc/apache2/sites-enabled# cd ..
root@debian:/etc/apache2# ls
apache2.conf conf-available conf-enabled envvars magic mods-available mods-enabled ports.conf sites-available sites-enabled tls
root@debian:/etc/apache2# vi apache2.conf
root@debian:/etc/apache2# cd sites-enabled/
root@debian:/etc/apache2/sites-enabled# ls
000-default.conf default-ssl.conf
root@debian:/etc/apache2/sites-enabled# vi default-ssl.conf
root@debian:/etc/apache2/sites-enabled# service apache2 start
root@debian:/etc/apache2/sites-enabled# cd /etc/
root@debian:/etc# ls
root@debian:/etc# cd /etc/apache2/tls
root@debian:/etc/apache2/tls# openssl genrsa 2048 > web.key
Generating RSA private key, 2048 bit long modulus (2 primes)
………………………………………………………………………………………………………………..+++++
…………………………………………………………………………..+++++
e is 65537 (0x010001)
root@debian:/etc/apache2/tls# openssl req -new -key web.key > web.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [AU]:FR
State or Province Name (full name) [Some-State]:BZH
Locality Name (eg, city) []:Lostihuel
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Ministère désarmé
Organizational Unit Name (eg, section) []:IT
Common Name (e.g. server FQDN or YOUR name) []:127.0.0.1
Email Address []:laurent@laurent.fr
Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
root@debian:/etc/apache2/tls# openssl genrsa 2048 > ca.key
Generating RSA private key, 2048 bit long modulus (2 primes)
..+++++
……………………………………………………………+++++
e is 65537 (0x010001)
root@debian:/etc/apache2/tls# openssl req -new -x509 -days 365 -key ca.key > ca.crt
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [AU]:FR
State or Province Name (full name) [Some-State]:BZH
Locality Name (eg, city) []:Lostihuel
Organization Name (eg, company) [Internet Widgits Pty Ltd]:BZH CA
Organizational Unit Name (eg, section) []:IT
Common Name (e.g. server FQDN or YOUR name) []:BZH CA
Email Address []:lm@lm.fr
root@debian:/etc/apache2/tls# openssl x509 -req -in web.csr -out web.crt -CA ca.crt -CAkey ca.key -CAcreateserial -CAserial ca.srl
Signature ok
subject=C = FR, ST = BZH, L = Lostihuel, O = Minist\C3\83\C2\A8re d\C3\83\C2\A9sarm\C3\83\C2\A9, OU = IT, CN = 127.0.0.1, emailAddress = laurent@laurent.fr
Getting CA Private Key
root@debian:/etc/apache2/tls# ls -lart
total 40
-rw——- 1 root root 948 Oct 27 18:40 servwiki.crt
-rw-r–r– 1 root root 887 Oct 28 11:12 macle.key
drwxr-xr-x 9 root root 4096 Oct 28 11:35 ..
-rw-r–r– 1 root root 1679 Oct 28 11:55 web.key
-rw-r–r– 1 root root 1070 Oct 28 11:58 web.csr
-rw——- 1 root root 1675 Oct 28 12:04 ca.key
-rw-r–r– 1 root root 1383 Oct 28 12:06 ca.crt
-rw-r–r– 1 root root 1306 Oct 28 12:07 web.crt
-rw-r–r– 1 root root 41 Oct 28 12:07 ca.srl
root@debian:/etc/apache2/tls# chmod 600 web.*
root@debian:/etc/apache2/tls# ls -lart
total 40
-rw——- 1 root root 948 Oct 27 18:40 servwiki.crt
-rw-r–r– 1 root root 887 Oct 28 11:12 macle.key
drwxr-xr-x 9 root root 4096 Oct 28 11:35 ..
-rw——- 1 root root 1679 Oct 28 11:55 web.key
-rw——- 1 root root 1070 Oct 28 11:58 web.csr
-rw——- 1 root root 1675 Oct 28 12:04 ca.key
-rw-r–r– 1 root root 1383 Oct 28 12:06 ca.crt
-rw——- 1 root root 1306 Oct 28 12:07 web.crt
-rw-r–r– 1 root root 41 Oct 28 12:07 ca.srl
drwxr-xr-x 2 root root 4096 Oct 28 12:07 .
root@debian:/etc/apache2/tls# rm servwiki.crt
root@debian:/etc/apache2/tls# rm macle.key
root@debian:/etc/apache2/tls# cd ..
root@debian:/etc/apache2# ls
apache2.conf conf-available conf-enabled envvars magic mods-available mods-enabled ports.conf sites-available sites-enabled tls
root@debian:/etc/apache2# cd sites-enabled/
root@debian:/etc/apache2/sites-enabled# ls
000-default.conf default-ssl.conf
root@debian:/etc/apache2/sites-enabled# vi default-ssl.conf
root@debian:/etc/apache2/sites-enabled# service apache2 restart
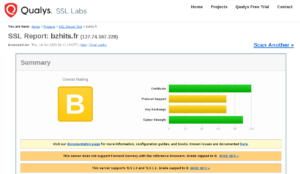
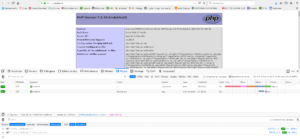
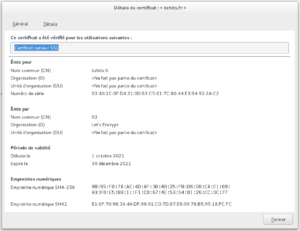
2 – Etape 2 avec un certificat signé par let’s encrypt
C’est plus compliqué car votre serveur doit avoir un nom de domaine que Let’s encrypt vérifiera (bref ne présente pas d’intérêt dans le cadre de la découverte de TLS)